What is a Security & Cloud Risk Assessment & Why Would You Want One?

As we wrote in a recent blog, no business is immune to cyber security threats. Cyber security risks are now higher than they’ve ever been, and lower than they ever will be.
But you can’t mitigate risks until you know what they are. You can’t fix problems you’re not aware of. Like a leak in the foundation of your home, a cyber security threat could cause trouble unbeknownst to you for months or even years… until it results in debilitating, expensive damage.
Fortunately, there are many ways to reduce your risks, and one of the best is with a security & cloud risk assessment. We’ll cover what it is and answer many key questions such as who needs one and how long it takes.
What is the Purpose of a Security & Cloud Risk Assessment?
Comprehensive cyber security assessments help you take the steps needed to stay ahead of prevalent threats. An assessment considers your business goals, compliance requirements and risk tolerance to build the security posture that aligns with your unique needs.
Organizations using cloud infrastructure retain responsibility for securing the data they put in the cloud in the well-known “shared responsibility model.” The impacts of your responsibilities are substantial, considering through 2025, 99% of cloud security failures will be the customer’s fault, according to Gartner. Cyber security assessments help organizations to better understand their responsibilities versus those of the cloud service provider. This information helps you reduce your risk of suffering a data breach and becoming a headline.
Who Needs a Security & Cloud Risk Assessment?
Simply put, if you’ve got electronic data, you could benefit from an assessment. Yes, even a landscaping company – check out our anecdote below. But the following are some specific reasons that might drive you to move forward.
- New Business Needs & Opportunities: New opportunities can often make your organization subject to new regulations. If you expand into California, you’ll need to comply with CCPA. Wursta consulted with an accounting firm that began serving doctors’ offices, and thus needed HIPAA compliance.
- Settings Drift: Over time, particularly with growing organizations, settings are likely to drift away from ideal best practices. Drift can occur due to careless admins, or simple human error in failing to understand the consequences of upgrades. Whatever the cause, an assessment will uncover risky drift, so you can maintain ideal posture.
- Change in Regulations: Worldwide, there are increases in both oversight and the specificity of cyber security regulations. For example, public companies that are subject to the reporting requirements of the Securities Exchange Act of 1934 may face additional new requirements. The SEC is proposing rules to enhance and standardize disclosures regarding cyber security risk management, strategy, governance, and cyber security incident reporting. Other new regulations include the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA), and the 2022 EU Cyber Resilience Act.
- New Tech: A new solution, such as a SaaS application, requires configuration, of course. However, with integrations and sharing capabilities, one new app can have a broad impact. For example, once a new marketing automation tool has access to your customer data, it could become a critical new attack vector.
- Avoid Legal Action & Bad Press: Organizations are subject to a variety of regulations, requiring them to protect customer data, such as FTC Fair Trade Practices for Privacy and Security. And no organization wants the reputational damage of being responsible for leaked customer data, exposing customers to risks like identity theft.
- Audit Preparation: Audits can be stressful and unpredictable. An assessment can help you prepare in advance of an official external audit. Although Wursta is not a certified audit firm, we can still help with preparation.
- Merger & Acquisition (M&A): Prior to an acquisition, companies want to evaluate risks to confirm the acquired company’s data is protected correctly. In the case of a divestiture, assessments can help identify the appropriate information to divest and isolate.
Many of these reasons would cause an organization to repeat an assessment. Assessments are not a “one-and-done” task.
Yes, Even the Landscaper Needs Cyber Hygiene
The Cyber Security Maturity Model Certification (CMMC) is a set of standards developed by the Department of Defense (DOD) for doing business with the department. Every DOD contract requires a specified CMMC level.
Yes, every contract.
Katie Arrington, CISO OUSD A&S, shared an interesting anecdote describing how a landscaping company doing lawn care at a military base doubted the need for cyber security. That need was quickly revealed with one question: “How do you bid the work?” The company was sent an AutoCAD plan of the fence and square footage of the base. Clearly, possession of this information necessitates basic cyber security hygiene.
What Happens During a Security & Cloud Risk Assessment?
Assessments should be based on a cyber security framework; for example the NIST CSF (National Institute of Standards and Technology Cyber security Framework.) “The Framework is based on existing standards, guidelines, and practices for organizations to better manage and reduce cyber security risk.” NIST CSF was designed to be voluntarily implemented, but many regulations, such as CMMC and HIPAA, are based on the Framework.
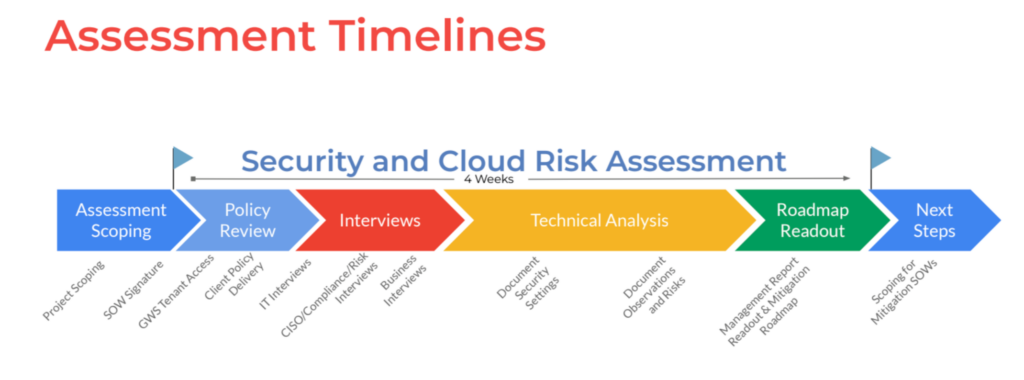
The Wursta S&CRA evaluates your essential security settings and general controls, reviews your cyber policies and procedures, and measures against industry best practice. That involves reviewing:
- Privileged access
- Security settings and alerting
- Endpoint management
- Google Drive audit and sharing
Visit our Security & Cloud Risk Assessment service web page for a complete list.
The assessment should also identify any relevant governance requirements and evaluate your security awareness and user behaviors via interviews. Interviews can include members of your accounting, IT, and HR teams.
How Long Does a Security & Cloud Risk Assessment Take?
A typical timeline is about four to six weeks.
What Happens After a Security & Cloud Risk Assessment?
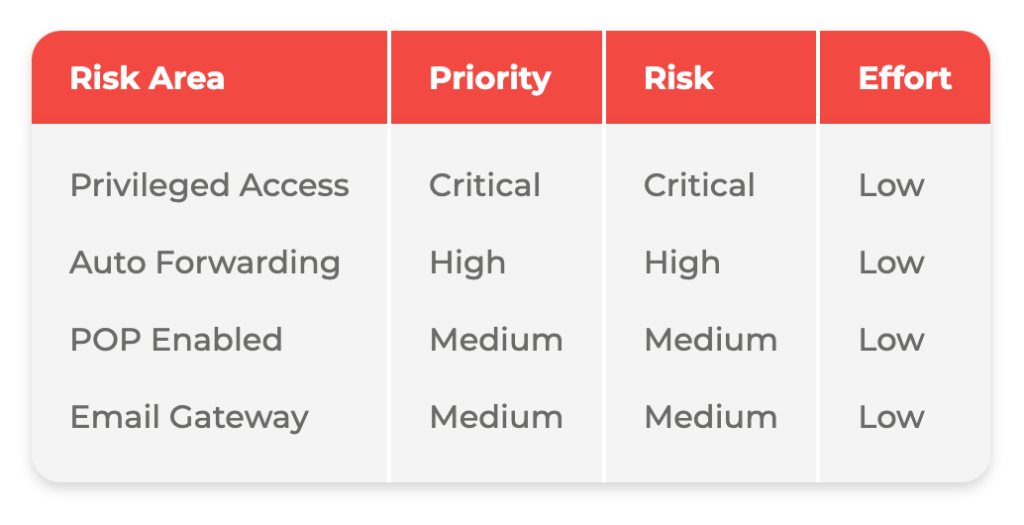
- Roadmap to Ideal Posture: An S&CRA informs you of any shortcomings and provides a roadmap to your ideal security posture. Assessments clarify the potential impact of risks and expose risks you may not have seen.
- Prioritized Recommendations: For any deviations from best practice, your vendor should recommend a detailed course of action to mitigate risk and comply with relevant regulations. Wursta also prioritizes the severity of issues to help your team determine what to address first, all while leveraging the numerous, powerful security tools offered by Google and other tools as needed.
- Informed Decision Making: Wursta takes the time to clearly lay out every option so you can make informed decisions. Suggestions include implementing and modifying the relevant technical controls, such as access controls, identity management, and security monitoring.
Look Out for What is Not a Security & Cloud Risk Assessment
A quick note on what is not an S&CRA: Regulatory audits will often go through a checklist such as timely termination of user accounts, but will fail to examine crucial areas like sharing settings. While such an audit can confirm you check all the boxes to comply with regulations, they ignore key issues that could present significant risk. This is often the case with audits done by huge firms such as the Big Four audit firms.
Additionally, an assessment is a detective process and typically does not include mitigation of the risks discovered. Perhaps you’ll receive top marks and your S&CRA will reveal your exemplary security posture, and therefore no mitigations would be needed. Whatever the outcome, Wursta is happy to help our clients offload part or all of the mitigation measures recommended, but it is a separate project with separate fees.
How do you Choose a Security & Cloud Risk Assessment Vendor?
Well, you’re already on Wursta’s site, so there’s no need to search further! Just go ahead and click, “Contact Us.” Wursta assists businesses of all sizes with a full suite of compliance and cyber security services that can be customized to fit your needs.
But seriously though, some reasons we may be a good fit include the fact that Wursta is a Premier Google partner. We have the broad expertise to resolve just about any Google Workspace and Google Cloud issue.
Additionally, our team members have a variety of expertise and certifications, including CMMC and certified ethical hackers. While not every regulation may be relevant to your organization, our expertise enables us to bring deep insights to every assessment.



